Introducing the End Point AI Portal for Our Customers

Today, End Point is opening up the End Point AI Portal for our customers to use. As a technology consulting company that gets in the trenches with our customers to integrate, manage, and support the information technology they need to operate and transform their businesses, we believe this is a great service for us to provide.
We are offering our AI Portal to our customers at no charge. The price is certainly right, so we think our customers are very much going to want to use it. 🙂
What’s in the Portal
End Point’s AI Portal provides an interface to interact with many different LLM AI chatbot services all in one place. It even gives users the ability to simultaneously submit queries and instructions to multiple LLMs and see their responses side by side.
Our Portal is a customized implementation of the Open WebUI AI interface and connects via APIs to various AI services. Because of this architecture, our analysis has shown that unless there is ongoing high-intensity usage, the cost per user will be very low — much lower than a typical end-user subscription to a single LLM provider. In the future we may implement an accounting system for the portal to pass usage costs onto our …
artificial-intelligence company
How to Analyze Application Logs and Extract Actionable Insights

Photo by Timo C. Dinger on Unsplash
Logs often accumulate unnoticed—until something breaks. Then, they suddenly become vital tools for diagnosing issues. By combining just a few command-line techniques, you can quickly spot recurring problems, identify suspicious activity, and strengthen your application’s defenses.
Below is a sample error log we’ll reference in the examples:
[2025-01-01 12:34:56] [client 192.168.1.1:12345] PHP Notice: Undefined variable $foo in /var/www/html/index.php on line 45 | referer: http://example.com/index.php
[2025-01-01 12:34:56] [client 192.168.1.1:12345] PHP Notice: Undefined variable $foo in /var/www/html/index.php on line 45 | referer: http://example.com/index.php
[2025-01-01 12:34:57] [client 192.168.1.1:12345] PHP Notice: Undefined variable $foo in /var/www/html/index.php on line 45 | referer: http://example.com/index.php
[2025-01-01 12:35:00] [client 10.0.0.2:6789] PHP Warning: Division by zero in /var/www/html/script.php on line 23 | referer: http://example.com/script.php
[2025-01-01 13:35:01] [client 10.0.0.2:6789] PHP Warning: Division by zero in /var/www/html/script.php on line 23 | referer: http://example.com/script.php
[2025-01-01 13:36:10] …logging automation monitoring security php shell
Resolving iptables Update Issues on Rocky Linux and Other RHEL-Based Systems

If you are on iptables-legacy systems, you may encounter errors when attempting to perform an OS update involving iptables-libs-1.8.10-11.el9_5.x86_64 on Rocky Linux or other Red Hat-based operating systems:
Error:
Problem: cannot install both iptables-libs-1.8.10-11.el9_5.x86_64 from baseos and iptables-libs-1.8.10-4.el9_4.x86_64 from @System
- package iptables-legacy-1.8.10-4.1.el9.x86_64 from @System requires (iptables-libs(x86-64) = 1.8.10-4.el9 or iptables-libs(x86-64) = 1.8.10-4.el9_4), but none of the providers can be installed
- cannot install the best update candidate for package iptables-libs-1.8.10-4.el9_4.x86_64
- cannot install the best update candidate for package iptables-legacy-1.8.10-4.1.el9.x86_64
(try to add '--allowerasing' to command line to replace conflicting packages or '--skip-broken' to skip uninstallable packages or '--nobest' to use not only best candidate packages)Cause of the error
The latest package, iptables-libs-1.8.10-11.el9_5.x86_64, is incompatible with iptables-legacy. To proceed with the update, you must remove iptables-legacy and transition to iptables-nft, which uses the nf_tables kernel API while …
redhat iptables sysadmin
The Case of the Mistimed Python Script

“Time isn’t working right!” said a message from a client on their internal chat.
My efforts to catch a spot as an extra in a Doctor Who episode have thus far been fruitless, so I jumped in to reply to that message. Just in case.
The follow-up had more detail: “I’ve set something to run at 7:30 AM every morning, but it runs at 2:30 AM instead. Time zone is right. I can’t figure out what’s wrong.”
Dang, the screen debut will have to wait. But at least this is a mystery I can solve.
The hypothesis offered up was that a Python script was getting the time wrong, but it turns out Python doesn’t do the scheduling here. Rather, it’s just plain ol’ cron, so all eyes are on that now.
First, the obvious: It’s running early, not late. So it’s not a situation where it’s running for about 5 hours and appearing later than desired. I mean, it could possibly be taking 19 hours to run and finishing at 2:30 the next day, but at a glance it’s clearly not taking that long. It’s just running at the wrong time.
Let’s double check what cron is actually set to do.
30 7 * * * python3 /home/data/process/something.pyAlright. So clearly cron is set for 7:30 but running that at the wrong time. That’s …
sysadmin linux tools
Place Labels in Cesium using Vector Data Tiles
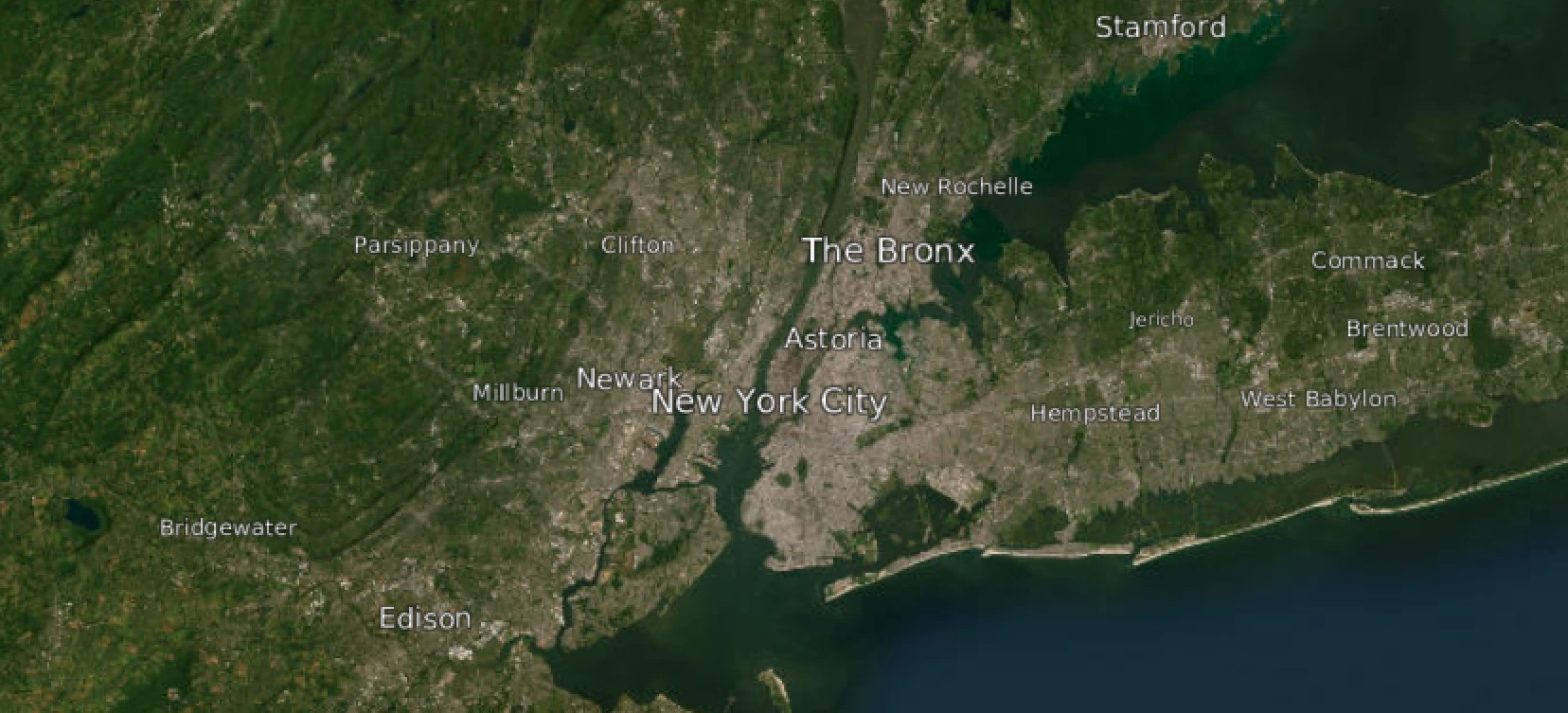
Cesium is like an IKEA globe: it can do almost anything, but you have to put it together yourself. One major missing feature is labels for cities. Compare the default views of Google Earth and Cesium, and you’ll notice this immediately.
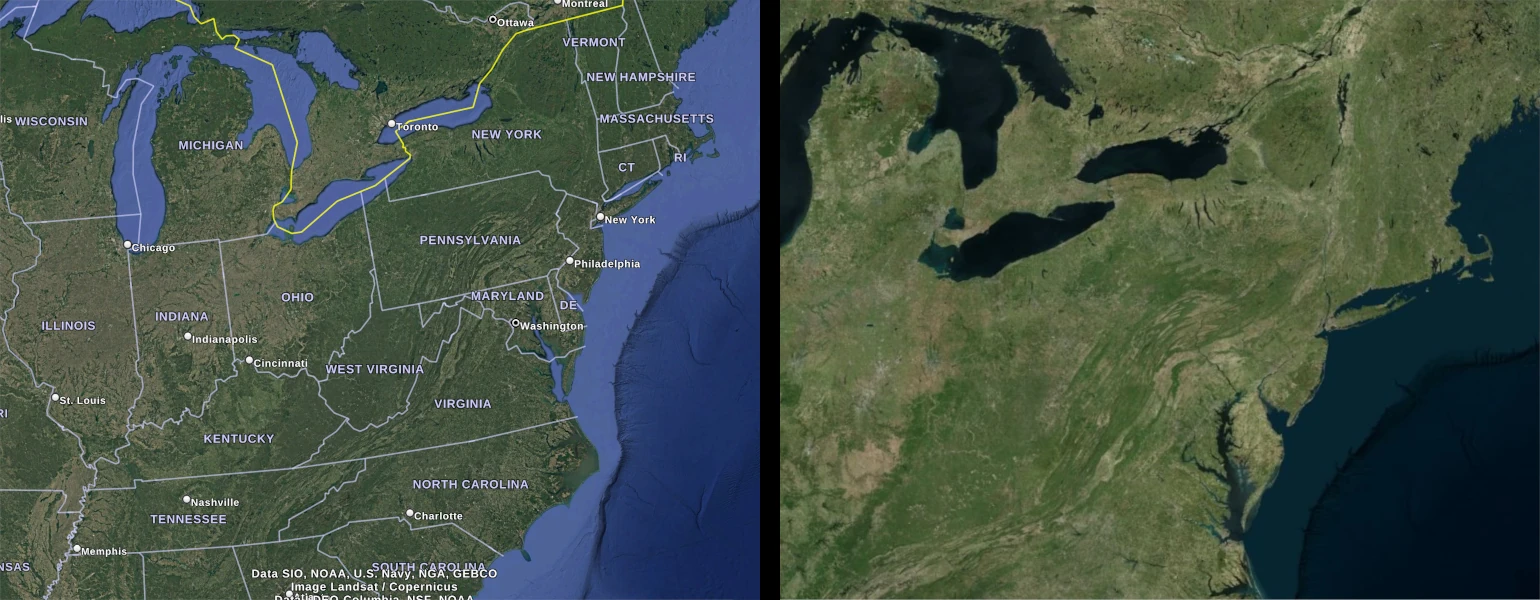
Left: Google Earth default view, with labels and state lines. Right: Cesium default view, with no labels or markers.
If you’re reading this post, you might be able to find any major U.S. city without any clues, but most people can’t. You can overlay imagery that includes labels as part of the image, but this approach has a significant drawback: as soon as you rotate the view away from north-up, the labels become difficult to read.
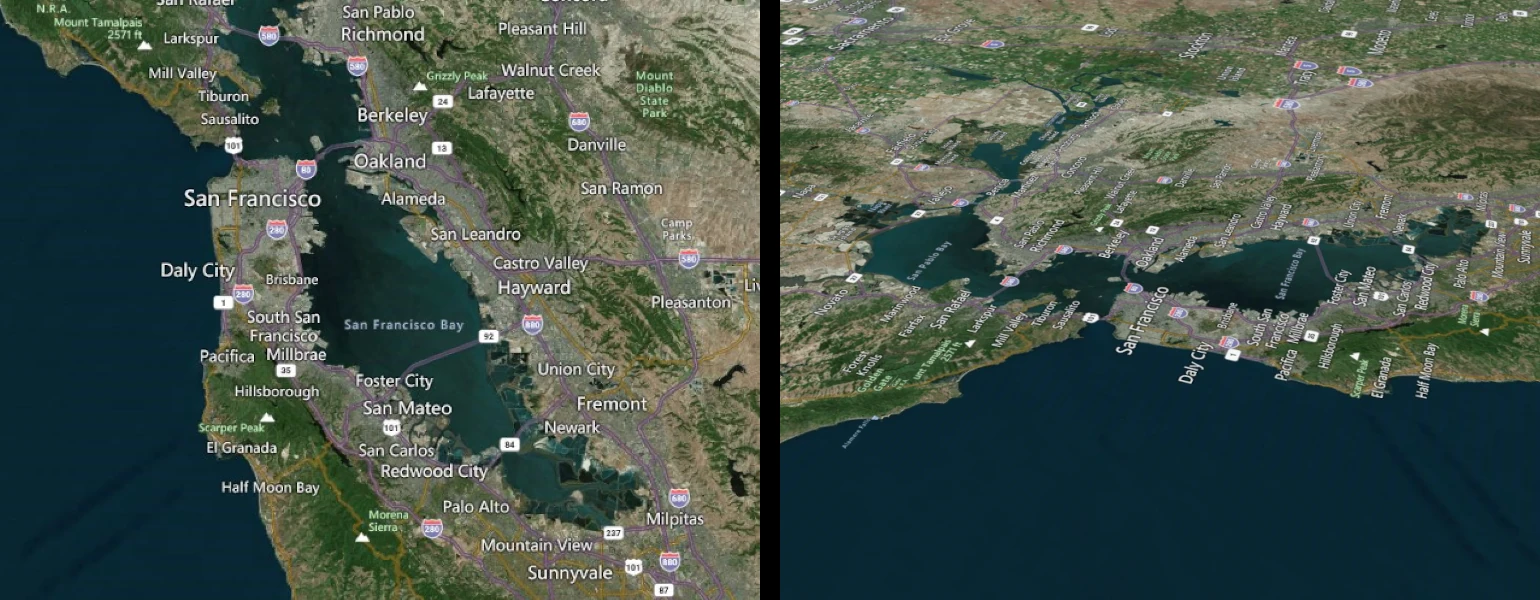
In Google Earth, this issue is handled using vector data overlays. Labels, borders, and other similar elements are examples of how useful vector overlays can be.
Cesium also supports vector features such as labels, polylines, and polygons. You can create them manually or use CZML or KML to add such features to a scene. If you use KML, Cesium translates it internally, but the result is the same. Vector features have distinct advantages for 3D geographic data, with …
cesium gis visionport open-source kml
Django and Mojolicious: a quick comparison of two popular web frameworks

Recently I’ve been working on a project with a Vue front-end and two back-ends, one in Python using the Django framework and one in Perl using the Mojolicious framework. So, it’s a good time to spend some words to share the experience and do a quick comparison.
Previously I wrote a post about Perl web frameworks, and now I’m expanding the subject into another language.
Django was chosen for this project because it’s been around for almost 20 years now and provides the needed maturity and stability to be long-running and low-budget. In this regard, it has proved a good choice so far. Recently it saw a major version upgrade without any problems to speak of. It could be argued that I should have used the Django REST Framework instead of plain Django. However, at the time the decision was made, adding a framework on top of another seemed a bit excessive. I don’t have many regrets about this, though.
Mojolicious is an old acquaintance. It used to have fast-paced development but seems very mature now, and it’s even been ported to JavaScript.
Both frameworks have just a few dependencies (which is fairly normal in the Python world, but not in the Perl …
perl python django mojolicious catalyst
Reducing page load times: Cloudflare and caching with ASP.NET

When designing the architecture for a new website, it’s important to keep caching in mind. Caching allows you to store a copy of the pages or resources used by your web application in your local browser. Content distribution networks such as Cloudflare also leverage cache directives to distribute content to users more efficiently.
If we are going to use response caching on our web application, we should not include anything that depends on the identity context for the user in the page content in the response. Instead, we should render the same content to every user that hits the same URL. If we include any identity-specific content, the CDN will reuse it for other requests, which is a security and privacy risk.
A simple example is an ecommerce site where the customer logs in to make a purchase: If the homepage shows the user name and icon at the top bar, that content should be rendered from a non-cached request. Otherwise, CDN caching will show the same user and icon to other visitors. And worse: depending on the validations applied to the website, the profile page could even display personal information to other users!
When dealing with these situations, I often rely on …
dotnet aspdotnet csharp cloudflare
Learning Vue 3 composables by creating an invoice generator

The latest major version of Vue, Vue 3, has new features that are not present in Vue 2, such as Teleport, Suspense, and support for multiple root elements per template. Vue 3 provides smaller bundle sizes, better performance, better scalability, and better TypeScript IDE support.
What are Vue 3 composables?
Writing repetitive code can be a real pain in the frontend development realm. We can use Vue 3 composables to encapsulate and reuse stateful logic in our components. In this blog post, we will look at how we can use composables to reuse business logic by building an invoice generator.
An invoice generator, simply said, is an application that creates and manages invoices. We will focus on creating Vue 3 composables to properly separate business logic while reusing it across different features.
Core functionalities for invoice generator
- Adding, editing, and removing invoices and items
- Calculating totals with discounts, taxes, and shipping
- Generating PDF invoices
To implement these functionalities, we’ll focus on:
- Creating composables to handle business logic
- Reusing this logic across features and components
Prerequisites
Basic understanding of:
- Vue 3 and Composition …
vue javascript frameworks programming







